“Thousands Across the U. S. Protest Trump Victory”. USA Today, November 10, 2016.
“Not My President, Thousands Say”, Washington Post, November 10, 2016
“Campuses Confront Hostile Acts Against Minorities After Donald Trump’s Election”, New York Times, November 10, 2016. (An article about how some Trump supporters are targeting minorities with hate crimes.)
I’ve rarely blogged here about political themes or issues (a notable exception: Last year when Trump slandered John McCain’s military service. I’m a retired Army Officer and that was too much.)
I’m also an unabashed Democrat and supporter of Hillary Clinton. I’m fiscally conservative – too often liberals and Democrats think government is the solution to every societal problem, and they implement new taxes or programs without thought about the negative effect of higher taxes on rents, housing prices and middle/low income wage earners.
But the election is over. Hillary Clinton won the popular vote. More voters felt she was the best choice for President. But, under the Constitution and the Electoral College, Donald Trump won the presidency. To the protestors and the Trump-supporter-hate-crime-perpetrators I say “Get Over It”.
To the protestors, I say: did you vote? Where were you over the last 6 months? Why didn’t you work on registering voters and getting out the vote before Tuesday November 8th rather than taking to the streets in virtually fruitless protests afterwards? Get involved in your government, your public safety and in politics starting today so you can really effect the change you want.
I could, like the protestors, write and scream about all the regressive laws and consequences which will take place over the next two years: repeal (rather than fixing) Obamacare, actions against immigrants (although, frankly, Obama deported more illegal immigrants than any prior President), backing away from climate change and environmental protection, and so forth.
But, to be honest, Donald Trump will be President and we all need to concentrate on common ground – on all the work that needs to be done to improve the safety, quality of life and economy of the United States.
 Here are some examples of such common ground:
Here are some examples of such common ground:
- Infrastructure. Both Clinton and Trump correctly proposed massive increases in spending on roads, bridges, utilities and other infrastructure. Let’s get together and do it.
- Cybersecurity. The Obama Administration has made great strides toward improving our cyber warfare and defense capabilities, and we need to do more. In particular, we need to protect our local and state governments, our financial institutions, our defense industries from the potential of a devastating cyberattack. Let’s get together and do it.
- Veterans. It is a serendipitous coincidence that I publish this post on Veterans’ Day, 2016. The terrible and stupid Iraq war perpetrated by the Bush-Cheney administration has resulted in hundreds of thousands of mentally- and physically-injured veterans. The Obama Administration has started to correct the awful way the VA Healthcare system has treated veterans, but we must do more. I support a son-in-law – a Marine with 100% disability – by buying him food and helping him with rent and care for his PTSD because his military disability pay and care is simply not sufficient for him to live in Seattle. But many veterans don’t have anyone to help them and end up homeless and wandering the street, causing problems for our police and paramedics and emergency rooms. For example, the Seattle Police Department alone has 10,000 encounters a year with people in crisis on the streets, many of them veterans. Let’s get together and fix this.
- Mental health and Opioid Addiction. Just as with veterans’ care, many people have mental health issues and/or are addicted to heroin, methamphetamine and other drugs. Up to 60% of the calls a Seattle police officer handles are people in crisis. This must be addressed and it is a bi-partisan issue. Republican Ohio Senator Rob Portman has made addressing opioid addiction a centerpiece of his campaign and his legislative agenda. Let’s get together and do it.
- FirstNet and support of our First Responders. I joined the First Responder Network Authority because I fervently believe in its mission to build a nationwide wireless network for public safety and our first responders. FirstNet was created by both Republicans and Democrats in bipartisan legislation passed in 2012. That legislation funded FirstNet with $7 billion from sale of spectrum to commercial carriers, and that same sale provided $35 billion or more to reduce the deficit. FirstNet will give first responders – indeed all public safety responders – the technology and tools they need to deal with many of the issues listed above, as well as crime, wildfires and emergency medical care. Let’s get together and do it.
- Internet of Things (IoT).
Many if not most of our electronics and gadgets will become part of the Internet of Things, perhaps 25 billion devices by 2020. Smart light bulbs, thermostats, DVD players and video cameras are just the start. Utilities will connect every water and gas and electric meter, transformers, valves and the rest of their infrastructure. Industry is creating whole manufacturing plants with every device connected. But IoT is a huge security risk, as shown by the Mirai IoT botnet attack of September 20th. IoT poses both great potential and risk for our society, and, frankly, the IoT needs to be regulated and secured as well as deployed. Let’s get together and do it. - The march of technology and loss of jobs. Much Presidential campaign rhetoric talked about the loss of jobs to China or Mexico. But, frankly, only 12% of the 5 million factory jobs the United States lost since 2000 have been lost to trade. A whopping 88% of the job loss is attributable to automation and robotics! Indeed, U.S. manufacturing output increased by 18% between 2006 and 2016, while the number of jobs decreased. The issue we need to address is finding living wage jobs which can co-exist with the never-ending march of technology and automation. Let’s get together and do it.
I agree, there is a time to protest, and I’m certain I will be in the streets at some point in the next two years.
But I’m also going to roll up my sleeves, find common ground on the issues I’ve listed above, and work to continue the improvements in the economy, quality of life, technology, infrastructure and public safety which have happened in the years since the beginning of the Great Recession (graphic at right).
I encourage you to join with me.
Let’s get together and do it.



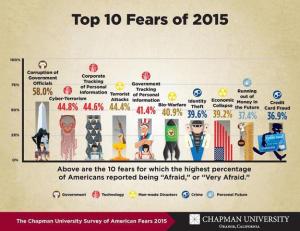 Americans fear government corruption more than anything else.
Americans fear government corruption more than anything else.






